Page 15 - Read Online
P. 15
Page 460 Phadke et al. Intell Robot 2023;3:453-78 https://dx.doi.org/10.20517/ir.2023.27
2.1. Adversarial environment applications
An adversarial environment is broadly defined as an environment where an agent may encounter any kind
of resistance to its activity or danger to its well-being. In such an environment, UAV swarms are expected to
face disruptions. However, an adversarial environment in military-specific applications is further
constructively defined as an environment where the swarm may be attacked by physical agents, such as
ground-based vehicles, projectiles, or other UAVs, in an attempt to impede its progress. Network attacks,
such as takeover and hacking attempts, or attempted swarm attacks by network jamming are also included.
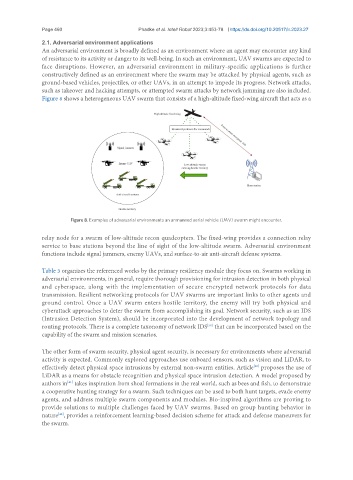
Figure 8 shows a heterogeneous UAV swarm that consists of a high-altitude fixed-wing aircraft that acts as a
Figure 8. Examples of adversarial environments an unmanned aerial vehicle (UAV) swarm might encounter.
relay node for a swarm of low-altitude recon quadcopters. The fixed-wing provides a connection relay
service to base stations beyond the line of sight of the low-altitude swarm. Adversarial environment
functions include signal jammers, enemy UAVs, and surface-to-air anti-aircraft defense systems.
Table 3 organizes the referenced works by the primary resiliency module they focus on. Swarms working in
adversarial environments, in general, require thorough provisioning for intrusion detection in both physical
and cyberspace, along with the implementation of secure encrypted network protocols for data
transmission. Resilient networking protocols for UAV swarms are important links to other agents and
ground control. Once a UAV swarm enters hostile territory, the enemy will try both physical and
cyberattack approaches to deter the swarm from accomplishing its goal. Network security, such as an IDS
(Intrusion Detection System), should be incorporated into the development of network topology and
routing protocols. There is a complete taxonomy of network IDS that can be incorporated based on the
[39]
capability of the swarm and mission scenarios.
The other form of swarm security, physical agent security, is necessary for environments where adversarial
activity is expected. Commonly explored approaches use onboard sensors, such as vision and LiDAR, to
[40]
effectively detect physical space intrusions by external non-swarm entities. Article proposes the use of
LiDAR as a means for obstacle recognition and physical space intrusion detection. A model proposed by
[41]
authors in takes inspiration from shoal formations in the real world, such as bees and fish, to demonstrate
a cooperative hunting strategy for a swarm. Such techniques can be used to both hunt targets, evade enemy
agents, and address multiple swarm components and modules. Bio-inspired algorithms are proving to
provide solutions to multiple challenges faced by UAV swarms. Based on group hunting behavior in
[42]
nature , provides a reinforcement learning-based decision scheme for attack and defense maneuvers for
the swarm.