Page 54 - Read Online
P. 54
Kim et al. J Surveill Secur Saf 2020;1:34-60 I http://dx.doi.org/10.20517/jsss.2020.14 Page 47
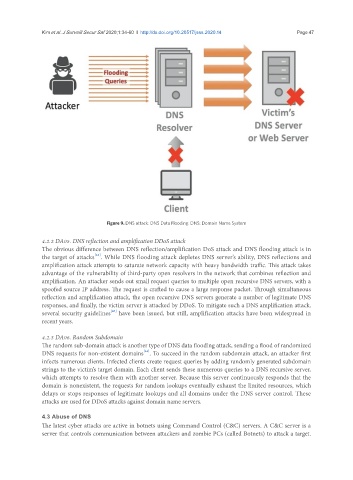
Figure 9. DNS attack: DNS Data Flooding. DNS: Domain Name System
4.2.2 DA05. DNS reflection and amplification DDoS attack
The obvious difference between DNS reflection/amplification DoS attack and DNS flooding attack is in
[42]
the target of attacks . While DNS flooding attack depletes DNS server’s ability, DNS reflections and
amplification attack attempts to saturate network capacity with heavy bandwidth traffic. This attack takes
advantage of the vulnerability of third-party open resolvers in the network that combines reflection and
amplification. An attacker sends out small request queries to multiple open recursive DNS servers, with a
spoofed source IP address. The request is crafted to cause a large response packet. Through simultaneous
reflection and amplification attack, the open recursive DNS servers generate a number of legitimate DNS
responses, and finally, the victim server is attacked by DDoS. To mitigate such a DNS amplification attack,
[43]
several security guidelines have been issued, but still, amplification attacks have been widespread in
recent years.
4.2.3 DA06. Random Subdomain
The random sub-domain attack is another type of DNS data flooding attack, sending a flood of randomized
DNS requests for non-existent domains . To succeed in the random subdomain attack, an attacker first
[44]
infects numerous clients. Infected clients create request queries by adding randomly generated subdomain
strings to the victim’s target domain. Each client sends these numerous queries to a DNS recursive server,
which attempts to resolve them with another server. Because this server continuously responds that the
domain is nonexistent, the requests for random lookups eventually exhaust the limited resources, which
delays or stops responses of legitimate lookups and all domains under the DNS server control. These
attacks are used for DDoS attacks against domain name servers.
4.3 Abuse of DNS
The latest cyber attacks are active in botnets using Command Control (C&C) servers. A C&C server is a
server that controls communication between attackers and zombie PCs (called Botnets) to attack a target.