Page 47 - Read Online
P. 47
Page 40 Kim et al. J Surveill Secur Saf 2020;1:34-60 I http://dx.doi.org/10.20517/jsss.2020.14
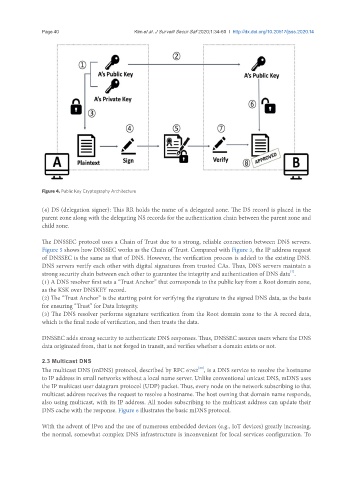
Figure 4. Public Key Cryptography Architecture
(4) DS (delegation signer): This RR holds the name of a delegated zone. The DS record is placed in the
parent zone along with the delegating NS records for the authentication chain between the parent zone and
child zone.
The DNSSEC protocol uses a Chain of Trust due to a strong, reliable connection between DNS servers.
Figure 5 shows how DNSSEC works as the Chain of Trust. Compared with Figure 3, the IP address request
of DNSSEC is the same as that of DNS. However, the verification process is added to the existing DNS.
DNS servers verify each other with digital signatures from trusted CAs. Thus, DNS servers maintain a
[7]
strong security chain between each other to guarantee the integrity and authentication of DNS data .
(1) A DNS resolver first sets a “Trust Anchor” that corresponds to the public key from a Root domain zone,
as the KSK over DNSKEY record.
(2) The “Trust Anchor” is the starting point for verifying the signature in the signed DNS data, as the basis
for ensuring “Trust” for Data Integrity.
(3) The DNS resolver performs signature verification from the Root domain zone to the A record data,
which is the final node of verification, and then trusts the data.
DNSSEC adds strong security to authenticate DNS responses. Thus, DNSSEC assures users where the DNS
data originated from, that is not forged in transit, and verifies whether a domain exists or not.
2.3 Multicast DNS
[20]
The multicast DNS (mDNS) protocol, described by RFC 6762 , is a DNS service to resolve the hostname
to IP address in small networks without a local name server. Unlike conventional unicast DNS, mDNS uses
the IP multicast user datagram protocol (UDP) packet. Thus, every node on the network subscribing to that
multicast address receives the request to resolve a hostname. The host owning that domain name responds,
also using multicast, with its IP address. All nodes subscribing to the multicast address can update their
DNS cache with the response. Figure 6 illustrates the basic mDNS protocol.
With the advent of IPv6 and the use of numerous embedded devices (e.g., IoT devices) greatly increasing,
the normal, somewhat complex DNS infrastructure is inconvenient for local services configuration. To