Page 9 - Read Online
P. 9
Page 110 Calderoni et al. J Surveill Secur Saf 2020;1:106-18 I http://dx.doi.org/10.20517/jsss.2019.01
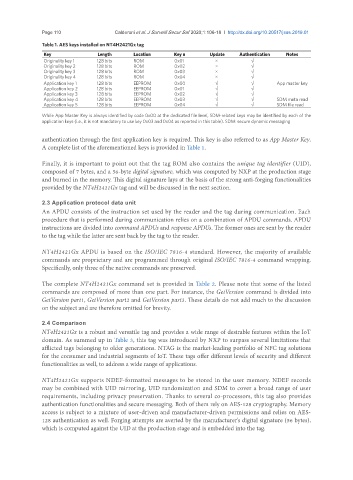
Table 1. AES keys installed on NT4H2421Gx tag
Key Length Location Key n Update Authentication Notes
Originality key 1 128 bits ROM 0x01 × √
Originality key 2 128 bits ROM 0x02 × √
Originality key 3 128 bits ROM 0x03 × √
Originality key 4 128 bits ROM 0x04 × √
Application key 1 128 bits EEPROM 0x00 √ √ App master key
Application key 2 128 bits EEPROM 0x01 √ √
Application key 3 128 bits EEPROM 0x02 √ √
Application key 4 128 bits EEPROM 0x03 √ √ SDM meta read
Application key 5 128 bits EEPROM 0x04 √ √ SDM file read
While App Master Key is always identified by code 0x00 at the dedicated file level, SDM-related keys may be identified by each of the
application keys (i.e., it is not mandatory to use key 0x03 and 0x04 as reported in this table). SDM: secure dynamic messaging
authentication through the first application key is required. This key is also referred to as App Master Key.
A complete list of the aforementioned keys is provided in Table 1.
Finally, it is important to point out that the tag ROM also contains the unique tag identifier (UID),
composed of 7 bytes, and a 56-byte digital signature, which was computed by NXP at the production stage
and burned in the memory. This digital signature lays at the basis of the strong anti-forging functionalities
provided by the NT4H2421Gx tag and will be discussed in the next section.
2.3 Application protocol data unit
An APDU consists of the instruction set used by the reader and the tag during communication. Each
procedure that is performed during communication relies on a combination of APDU commands. APDU
instructions are divided into command APDUs and response APDUs. The former ones are sent by the reader
to the tag while the latter are sent back by the tag to the reader.
NT4H2421Gx APDU is based on the ISO/IEC 7816-4 standard. However, the majority of available
commands are proprietary and are programmed through original ISO/IEC 7816-4 command wrapping.
Specifically, only three of the native commands are preserved.
The complete NT4H2421Gx command set is provided in Table 2. Please note that some of the listed
commands are composed of more than one part. For instance, the GetVersion command is divided into
GetVersion part1, GetVersion part2 and GetVersion part3. These details do not add much to the discussion
on the subject and are therefore omitted for brevity.
2.4 Comparison
NT4H2421Gx is a robust and versatile tag and provides a wide range of desirable features within the IoT
domain. As summed up in Table 3, this tag was introduced by NXP to surpass several limitations that
afflicted tags belonging to older generations. NTAG is the market-leading portfolio of NFC tag solutions
for the consumer and industrial segments of IoT. These tags offer different levels of security and different
functionalities as well, to address a wide range of applications.
NT4H2421Gx supports NDEF-formatted messages to be stored in the user memory. NDEF records
may be combined with UID mirroring, UID randomization and SDM to cover a broad range of user
requirements, including privacy preservation. Thanks to several co-processors, this tag also provides
authentication functionalities and secure messaging. Both of them rely on AES-128 cryptography. Memory
access is subject to a mixture of user-driven and manufacturer-driven permissions and relies on AES-
128 authentication as well. Forging attempts are averted by the manufacturer’s digital signature (56 bytes),
which is computed against the UID at the production stage and is embedded into the tag.