Page 10 - Read Online
P. 10
Calderoni et al. J Surveill Secur Saf 2020;1:106-18 I http://dx.doi.org/10.20517/jsss.2019.01 Page 111
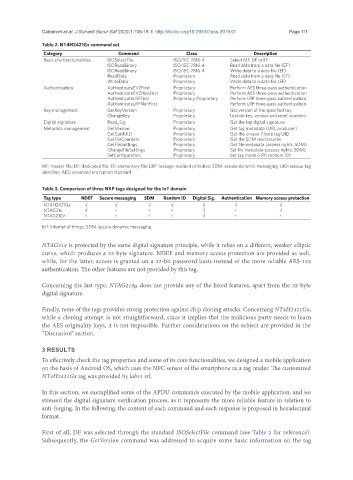
Table 2. NT4H2421Gx command set
Category Command Class Description
Basic r/w functionalities ISOSelectFile ISO/IEC 7816-4 Select MF, DF or EF
ISOReadBinary ISO/IEC 7816-4 Read data from a data file (EF)
ISOReadBinary ISO/IEC 7816-4 Write data to a data file (EF)
ReadData Proprietary Read data from a data file (EF)
WriteData Proprietary Write data to a data file (EF)
Authentication AuthenticateEV2First Proprietary Perform AES three-pass authentication
AuthenticateEV2NonFirst Proprietary Perform AES three-pass authentication
AuthenticateLRPFirst Proprietary Proprietary Perform LRP three-pass authentication
AuthenticateLRPNonFirst Perform LRP three-pass authentication
Key management GetKeyVersion Proprietary Get version of the specified key
ChangeKey Proprietary Update key, version and reset counters
Digital signature Read_Sig Proprietary Get the tag digital signature
Metadata management GetVersion Proprietary Get tag metadata (UID, producer)
GetCardUID Proprietary Get the unique 7-byte tag UID
GetFileCounters Proprietary Get the SDM read counter
GetFileSettings Proprietary Get file metadata (access rights, SDM)
ChangeFileSettings Proprietary Set file metadata (access rights, SDM)
SetConfiguration Proprietary Set tag mode (LRP, random ID)
MF: master file; DF: dedicated file; EF: elementary file; LRP: leakage-resilient primitive; SDM: secure dynamic messaging; UID: unique tag
identifier; AES: advanced encryption standard
Table 3. Comparison of three NXP tags designed for the IoT domain
Tag type NDEF Secure messaging SDM Random ID Digital Sig. Authentication Memory access protection
NT4H2421Gx √ √ √ √ √ √ √
NTAG21x √ × × × √ × √
NTAG210μ × × × × √ × ×
IoT: internet of things; SDM: secure dynamic messaging
NTAG21x is protected by the same digital signature principle, while it relies on a different, weaker elliptic
curve, which produces a 32-byte signature. NDEF and memory access protection are provided as well,
while, for the latter, access is granted on a 32-bit password basis instead of the more reliable AES-128
authentication. The other features are not provided by this tag.
Concerning the last type, NTAG210μ does not provide any of the listed features, apart from the 32-byte
digital signature.
Finally, none of the tags provides strong protection against chip cloning attacks. Concerning NT4H2421Gx,
while a cloning attempt is not straightforward, since it implies that the malicious party needs to learn
the AES originality keys, it is not impossible. Further considerations on the subject are provided in the
“Discussion” section.
3 RESULTS
To effectively check the tag properties and some of its core functionalities, we designed a mobile application
on the basis of Android OS, which uses the NFC sensor of the smartphone as a tag reader. The customized
NT4H2421Gx tag was provided by lab51 srl.
In this section, we exemplified some of the APDU commands executed by the mobile application, and we
stressed the digital signature verification process, as it represents the more reliable feature in relation to
anti-forging. In the following, the content of each command and each response is proposed in hexadecimal
format.
First of all, DF was selected through the standard ISOSelectFile command (see Table 2 for reference).
Subsequently, the GetVersion command was addressed to acquire some basic information on the tag