Page 89 - Read Online
P. 89
Page 82 Salmani et al. J Surveill Secur Saf 2020;1:79–101 I http://dx.doi.org/10.20517/jsss.2020.16
Index Query encryption
Files
Keyword Extraction
Data Owner
Data Users
Secret Key K
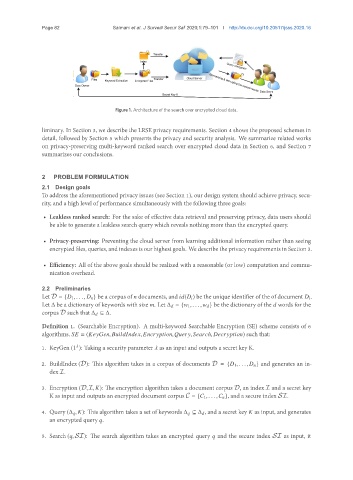
Figure 1. Architecture of the search over encrypted cloud data.
liminary. In Section 3, we describe the LRSE privacy requirements. Section 4 shows the proposed schemes in
detail, followed by Section 5 which presents the privacy and security analysis. We summarize related works
on privacy-preserving multi-keyword ranked search over encrypted cloud data in Section 6, and Section 7
summarizes our conclusions.
2 PROBLEM FORMULATION
2.1 Design goals
To address the aforementioned privacy issues (see Section 1), our design system should achieve privacy, secu-
rity, and a high level of performance simultaneously with the following three goals:
• Leakless ranked search: For the sake of effective data retrieval and preserving privacy, data users should
be able to generate a leakless search query which reveals nothing more than the encrypted query.
• Privacy-preserving: Preventing the cloud server from learning additional information rather than seeing
encrypted files, queries, and indexes is our highest goals. We describe the privacy requirements in Section 3.
• Efficiency: All of the above goals should be realized with a reasonable (or low) computation and commu-
nication overhead.
2.2 Preliminaries
Let D = {D 1 ,. . ., D n } be a corpus of n documents, and id(D i ) be the unique identifier of the of document D i.
Let ∆ be a dictionary of keywords with size m. Let ∆ d = {w 1 ,. . .,w d } be the dictionary of the d words for the
corpus D such that ∆ d ⊆ ∆.
Definition 1. (Searchable Encryption). A multi-keyword Searchable Encryption (SE) scheme consists of 6
algorithms, SE = (KeyGen, BuildIndex, Encryption,Query,Search, Decryption) such that:
λ
1. KeyGen (1 ): Taking a security parameter λ as an input and outputs a secret key K.
2. BuildIndex (D): This algorithm takes in a corpus of documents D = {D 1 ,. . ., D n } and generates an in-
dex I.
3. Encryption (D,I,K): The encryption algorithm takes a document corpus D, an index I and a secret key
K as input and outputs an encrypted document corpus C = {C 1 ,. . .,C n }, and a secure index SI.
4. Query (∆ q ,K): This algorithm takes a set of keywords ∆ q ⊆ ∆ d, and a secret key K as input, and generates
an encrypted query q.
5. Search (q,SI): The search algorithm takes an encrypted query q and the secure index SI as input, it